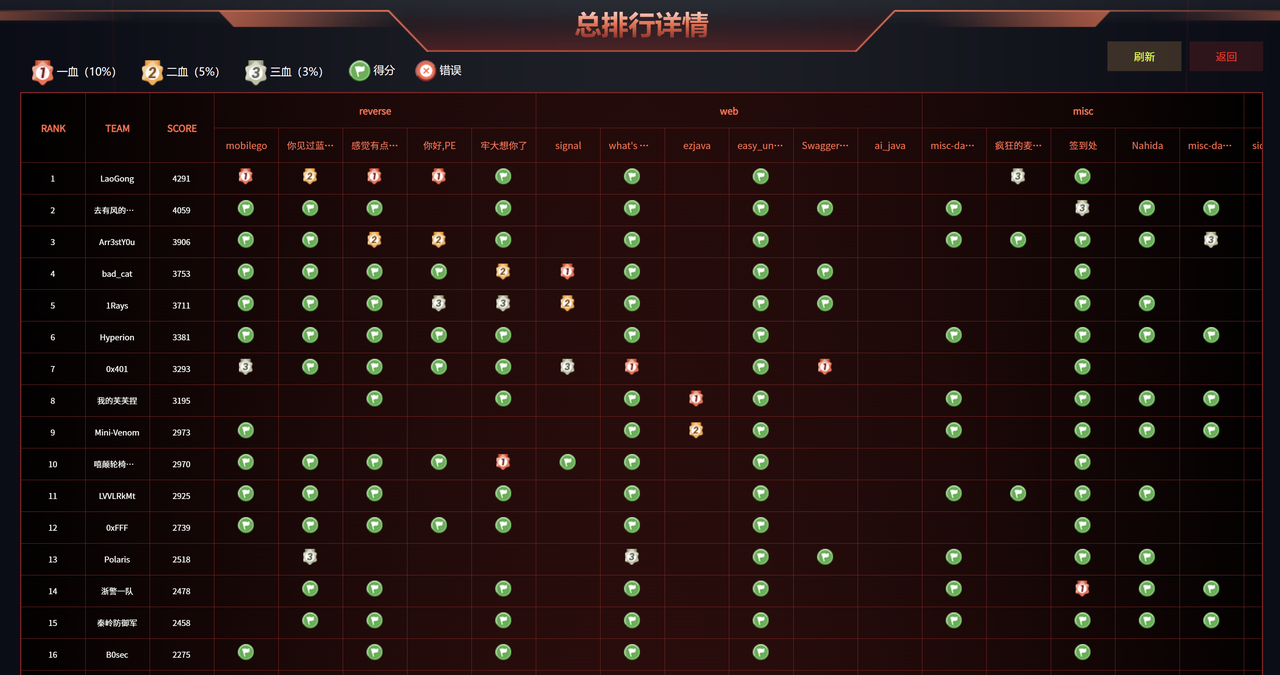
安洵杯wp-LVVLRkMt
Last Update:
安洵杯wp-LVVLRkMt
Pwn
side_channel , initiate!
思路OR缺W,打一个侧信道逐位爆破
1 | |
Seccomp
SROP+ORW解决
1 | |
web
what’s my name
本地搭建echo $miao发现lambda自增,那第二个if完全可控


easy_unserialize
__wakeup->__unset->__isset->__toString->__invoke
empty触发isset
preg_match触发toString
1 | |
Crypto
010101
- nc得到三个参数npc
- 然后看逻辑就是p替换了两个bit输出来了,爆破就行了【这个地方比赛环境当时有点问题,我卡了有半个小时,脚本没动,数据不对】
1 | |
Misc
签到

Nahida
- 逆转搞出图片
1 | |
然后,梭

疯狂的麦克斯
- docx变zip,后面文字rot22,加上提示base64
- 直接把列表所有元素rot22然后base64,再放进去爆破
1 | |

misc-dacong_no_windows
使用Imdisk工具将dacong.raw在电脑上挂载,并使用diskgenius的恢复功能恢复出挂载映像中的文件


flag有提示,分为三段,先找的flag2和flag3
得出的文件中flag2是个压缩包。
里面一句话
Once upon a time there were three girls, one with white hair, one with black hair, and one with green hair. In a cold winter, Xiao Bai and Xiao Hei hid Xiao Lu’s favorite green onions. Looking at the heavy snow outside the window, can you find where the green onions are?

解出来_tHE_Dddd
flag3是U2FsdGVkX18M+E34cKJlmTU3uo1lHqjUQhKPTBGJiMjg4RWX6saTjOJmLU8653
base64之后发现有Salted__字样,aes,密码在注册表里
d@@Coong_LiiKEE FOr3NsIc
解出来是dAc0Ng_SIst3Rs????}
flag1在恢复出的图形类里
RX-sstv结合音频39(初音未来懂得都懂)
图片里面flag{Ar3_Th3Y
合起来flag{Ar3_Th3Y_tHE_DddddAc0Ng_SIst3Rs????}
RE
mobilego
- so的check看了一会比较难崩,但是看flag的密文形式很像简单位置替换
- 所以直接输编码表,jeb动调然后得到替换表
- 解密就行
flag密文的话有string.cmp,直接追踪资源就行
1 | |

感觉有点点简单
- 文件sys挺吓人,实际就一个改了的RC4和base64,都不需要运行
- base改了爆破就行了,逆还得动脑子
1 | |
- RC4 64改写
1 | |
PE
- 有点可惜,但也正常,太久不看的人是这样的
- 动调call恢复function可以进入主逻辑,加密过程也很简单
- 就剩一张当时截的图,v5 < 0,8个字节一组进行处理

1 | |
牢大想你了
- 混淆的挺好,下次别混淆了
- manager/data定位核心dll,dotpeek反编译
- 找到Tea的密文和密钥,直接解密【花里胡哨的没用代码一大坨】
1 | |
你见过蓝色的小鲸鱼
- 题目提示了blowfish加密,那么第一步要做的就是确认代码是否是一个正常的加密
- 然后密钥UzBtZTBuZV9EMGcz
- 密文dump出来:11A51F049550E2508F17E16CF1632B47
- 在线网站直接解密

D0g3{UzBtZTBuZV9EMGczQHRoZWJsdWVmMXNo}